
A firewall is a type of gateway network system that keeps an eye on and regulates inbound and outgoi...
Know More
Endpoint security, also known as endpoint protection, refers to the strategy and technologies deploy...
Know More.jpg)
Data Loss Prevention (DLP) is a set of tools, policies, and practices designed to detect, prevent, a...
Know More.jpg)
Mobile Device Management (MDM) is a comprehensive strategy and technology solution that enables orga...
Know More
Device encryption is a security measure that protects data stored on electronic devices by convertin...
Know More
Email security encompasses the strategies, technologies, and best practices implemented to protect e...
Know More.jpg)
Web Application Firewall is a security solution designed to protect web applications from various cy...
Know More
PAM stands for Privileged Access Management. It is a cybersecurity solution that focuses on controll...
Know More
PIM security policies often focus on controlling users with elevated permissions to change settings,...
Know More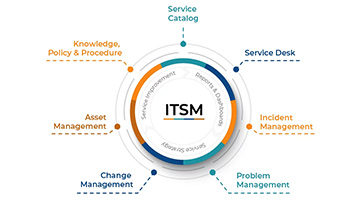
IT Asset Management (ITAM) is a vital element of IT Service Management (ITSM) that focuses on the ef...
Know More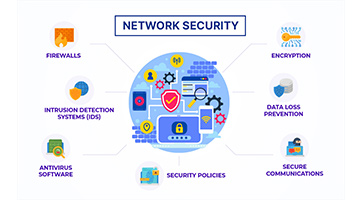
Network security involves policies, practices, and technologies designed to safeguard the integrity,...
Know More
Network health monitoring involves continuously tracking, analyzing, and managing your network&rsquo...
Know More